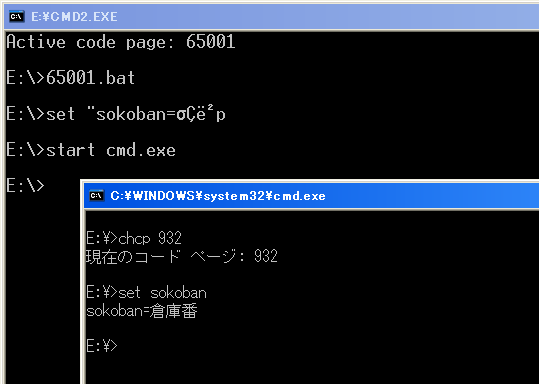
carlos wrote:penpen, i copy the comment from the source that explain:
Sorry, i've asked in a wrong way and missed how easy it is to misunderstand my above questions ...
(I wanted to ask short questions, but at least "forgotten" that you are not able to read my mind: I'm lacking in concentration because of bad headaches).
I should have asked in another way... .
Well i've read your documentation, used an dll-import-viewer to find the code location of MultiByteToWideChar (4AD01158).
Then i used a hex editor to search for 5811D04A (possible references to that function), and i saw that all are preceeded by "FF15", so all seems to be calls to that function (i cannot read all opcodes, but some looks familiar to me):
FF15 5811D04A == call ds:MultiByteToWideChar.
So you have changed the "dwFlags"-argument of the first two calls to MultiByteToWideChar, but you havent't changed the other 4 calls to that function:
Code: Select all
file offset | code offset | dwFlags set to
------------+-------------+----------------
5E57 | 4AD06A57 | 1
A477 | 4AD0B077 | 1
105CE | 4AD111CE | ebx ?= 0
162e6 | 4AD16EE6 | 1
1a3a5 | 4AD1AFA5 | ebx == 1
1c2dd | 4AD1CEDD | 1
So what i've wanted to know with my above questions:
'What is the cause of the bug?' ==
'Because you didn't change the "dwFlags"-argument of the other calls to MultiByteToWideChar, and
because you have written "dwFlags
should be 0",
i've assumed you've described in your documentation is just a side effect, and i wanted to know the real cause.'
'And what are the data values standing for, that your patch changes?' ==
'What does MB_PRECOMPOSED mean?'
(Well the second question was just because i was to lazy to use google, and i think you should know their meanings.)
@Aacini:
After you've found out to change the second parameter (i only assumed it is the second, i haven't looked it up),
you just have to find out, what's above the call (maybe using IntelIA-32 Architectures, Software Developer’s Manual, Volume 2, Instruction Set Reference, A-Z):
Code: Select all
FF75 F8 == push [ebp-8]
57 == push esi
6A 01 == push 1
FF35 ECB9D24A == push dword ptr [4A...]
I think carlos just interpreted as much as needed to make these hex offsets unique.
Intel 64 and IA-32 Architectures Software Developer Manuals could be downloaded from this location:
http://www.intel.com/content/www/us/en/processors/architectures-software-developer-manuals.html?iid=tech_vt_tech+64-32_manualspenpen
Edit1: Added the "Intel 64 and IA-32 Architectures Software Developer Manuals" link.
Edit2: I've changed the file location of the third call from (105C0, 4AD111C0) to the real value (E at the end instead of the 0).